CYBER LAW
INTRODUCTION:
In India,cyber laws are contained in the information technology act 2000 which came into force on oct 17,2000. The main purpose of the act is to provide legal recognition to electronic records with the government. None of the existing laws gave any legal vaildity or sanction to the activities in cyberspace . The computer generated world of internet is known as cyberspace and the lawa prevailing this are known as cyber law.
DEFINITION OF CYBER CRIME
Cyber crime is not defintion in IT Act 2000 nor in the national cyber security policy 2013 nor in any other regulation in India . In general cybercrime may be defined as ”Any unlawful act where computer or communication device or computer network is used to comit or facilitate the commisiion of crime”.
NEED FOR THE CYBER LAW IN INDIA:
Cyber law is important because it touches almost all aspects of transactions and activities and on involving the internet, world wide web and cyber space. Every action and reaction in cyberspace has some legal and cyber legal angles.
People are becoming more and more digitally sophisticated d and so are the crimes. As the number of internet users in on rise, the need for cybercrime laws and their application has also gathered great momentum.
# Almost all transactions in shares are in demat form.
# Almost all companies extensively depend upon their computer networks and keep their valuable data in electronic form.
# Government forms including income tax returns, company law forms etc. are now filled in electronic form.
# Consumers are increasingly using credit/debit cards for shopping.
# Most people are using email, phones and SMS messages for communication.
# Even in “non-cyber crime” cases, important evidence is found in computers/cell phones eg: in cases of murder, divorce, kidnapping, tax evasion, organized crime, terrorist operations, counterfeit currency etc.
# Cybercrime cases such as online banking frauds, online share trading fraud, source code theft, credit card fraud, tax evasion, virus attacks, cyber sabotage, phishing attacks, email hijacking, denial of service, hacking, pornography etc. are becoming common.
# Digital signatures and e-contracts are fast replacing conventional method of transacting business.
CLASSIFICATION OF CYBER CRIMES
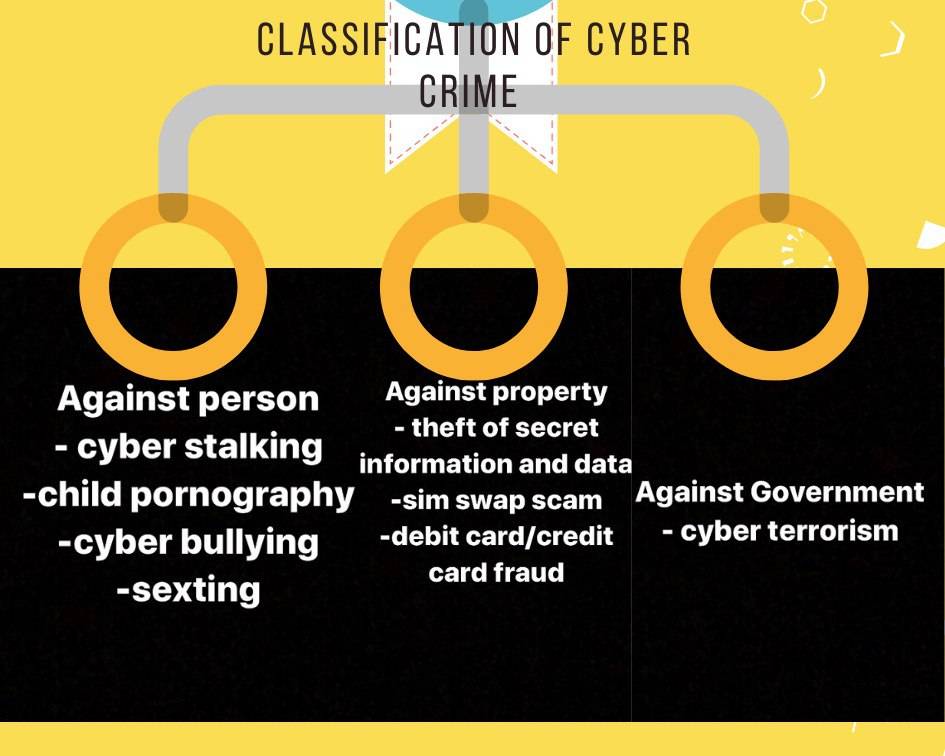
CYBER CRIME AGAINST PERSON-
# child pornography –
Or say child sexually abusive material (CSAM) refers to material containing sexual image in any form , of a child who is abused or sexually exploited. Section 67(B) of IT act states that it is punishable for publishing or transmitting of material depicting children in sexually explicit act etc.
#Cyber bullying-
it is form of harassment or bullying inflicted through the use of electronic or communication devices such as computer , mobile phones , laptop, etc it includes behaviour like posting rumours, threats , sexual remarks, a victims personal information . Bullying can be identified by repeated behaviour and an intent to harm .
#cyber stalking– the use of electronic communication by a person to follow , a person , or attempts to contact a person to foster personal interaction repeatedly despite a clear indication of disinterest by such person , or monitors the internet , commits the offence of stalking .
# sexting– sexting is an act of sending sexually explicit digital images , videos, text messages, or emails, usually by cell phone.
Crime against government-
# cyber terrorism– it is one distinct kind of crime in this category. The medium of cyber space is used by individuals and groups to threaten the international govt. This crime manifest itself into terrorism when an individual “cracks” into a government or military maintained website . Introducing viruses to vulnerable network , website defacing , Denial of service attacks and terroristic threats made via email are also include against government.
Crime against property-
#SIM SWAP SCAM
SIM Swap Scam occurs when fraudsters manage to get a new SIM card issued against a registered mobile number fraudulently through the mobile service provider. With the help of this new SIM card, they get One Time Password (OTP) and alerts, required for making financial transactions through victim’s bank account. Getting a new SIM card against a registered mobile number fraudulently is known as SIM Swap.
# DEBIT/CREDIT CARD FRAUD
Credit card (or debit card) fraud involves an unauthorized use of another’s credit or debit card information for the purpose of purchases or withdrawing funds from it.
#INTERPERSONAL AND IDENTITY THEFT
Impersonation and identity theft is an act of fraudulently or dishonestly making use of the electronic signature, password or any other unique identification feature of any other person.
1. Use strong passwords
2. Keep your software updated
3.Manage your social media settings
Keep your personal and private information locked down
4. Strengthen your home network
It’s a good idea to start with a strong encryption password as well as a virtual private network. A VPN will encrypt all traffic leaving your devices until it arrives at its destination. If cybercriminals do manage to hack your communication line, they won’t intercept anything but encrypted data. It’s a good idea to use a VPN whenever you a public Wi-Fi network, whether it’s in a library, café, hotel, or airport.
5.Talk to your children . Make sure they know that they can come to you if they’re experiencing any kind of online harassment, stalking, or bullying.
6. Keep up to date on major security breaches
If you do business with a merchant or have an account on a website that’s been impacted by a security breach, find out what information the hackers accessed and change your password immediately.
7.Take measures to help protect yourself against identity theft
CONCLUSION-
To sum up , Technology is always a double edged sword can be used for both the purposes good or bad . Hence, it should be the efforts of law makers to ensure that technology grows in a healthy manner and is used for legal and ethical business growth and not for committing crimes and also the duty of society playing their respective role within the permitted limitations and ensuring obedience with the law of land .
REFERENCES
•National Cybercrime Reporting Portal
•Norton
•www. Legal service india.com
Author: Mahima,
1st year faculty of law , Delhi university


3 thoughts on “Cyber crimes”